KaPingYee asks: What's unsafe about the Web and how can we fix it?
He'll give a rundown of some of the current proposed solutions for phishing, offer my thoughts on their strengths and weaknesses, and present a recent idea he had that he calls "passnames". Then we can open the floor to discussion. Ping has mainly been looking at the phishing problem, but feel free to suggest other big problems to talk about and your ideas for dealing with them.
Check out the anti-fraud mailing list: http://lists.cacert.org/cgi-bin/mailman/listinfo/anti-fraud
With passnames, you don't enter passwords into password fields anymore. You just enter a *passname* (which is an at-sign followed by the name of the site). You can choose whatever site names you want that make sense to you.
You only type in your secret password once, in a secure part of the browser interface, such as the menubar. The password your browser sends is a hash of the secret together with the site name. The browser automatically fills in the password field with the site name so you cannot type the wrong thing into the password field.
Screenshot (this is a mockup):
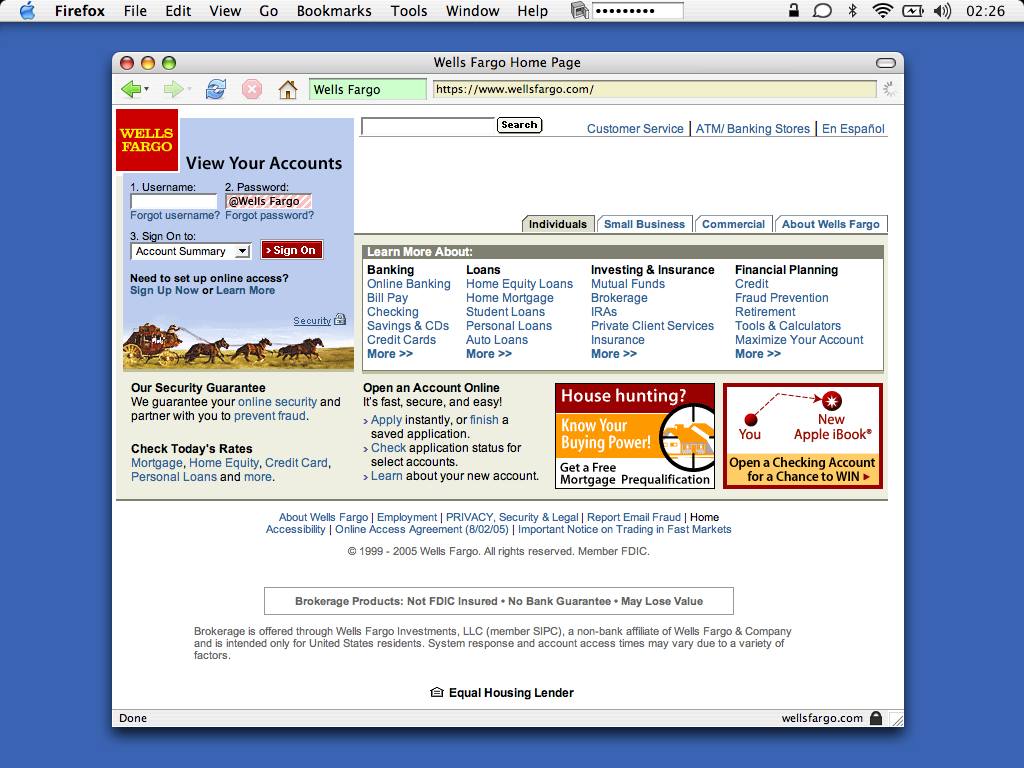
A label in front of the location bar (just like the petname tool at http://petname.mozdev.org/ ) tells you who you're talking to, to protect you from being fooled by an impersonator.
The browser knows when you are assigning a name to a new site, because in virtually all "change password" forms you're asked to enter the password twice. So when the browser sees you type the same passname into two consecutive password fields, it assigns that name as the name for the site.
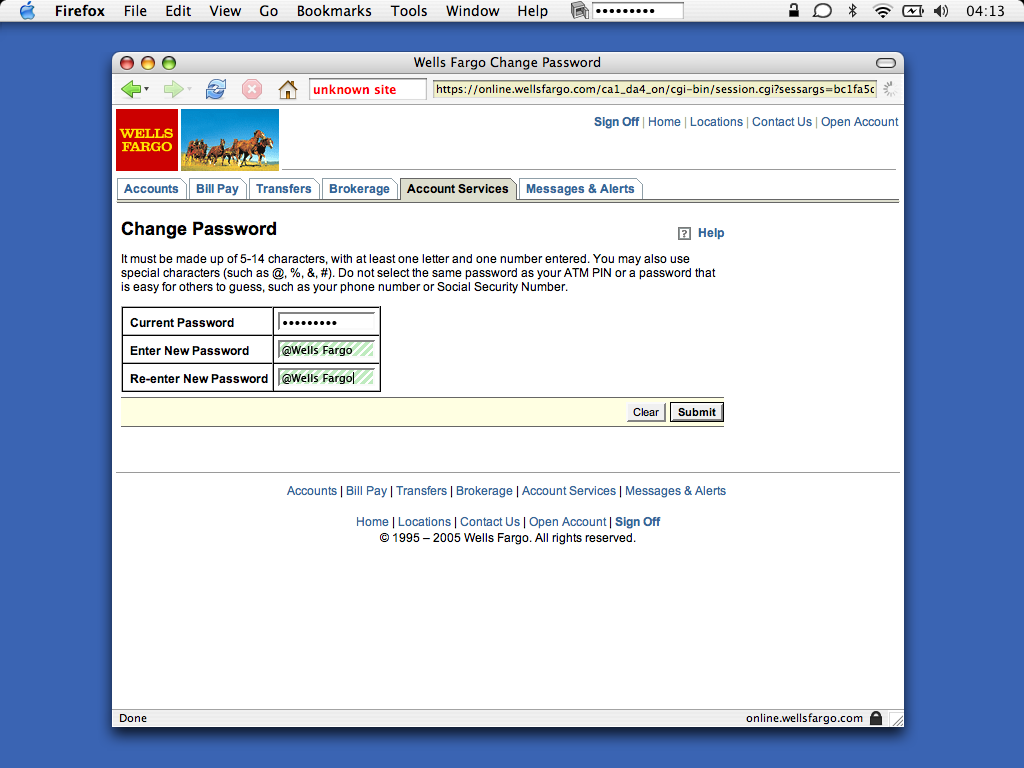
Suppose you already have an existing account at wellsfargo.com. To set up a passname, you just go there and change your password, but enter a passname as the new password. Here's what it would look like:
The passnames proposal has a few advantages over other proposals out there:
- You can migrate to the new scheme, one site at a time.
- You never enter any secrets in the document window. So you can't get your password sniffed by Javascript, Flash, or Java running in the downloaded page.
- You only have to remember one password.
- Every site gets a different hashed password, so if someone breaks into one site, they don't get your password for any of your other accounts.
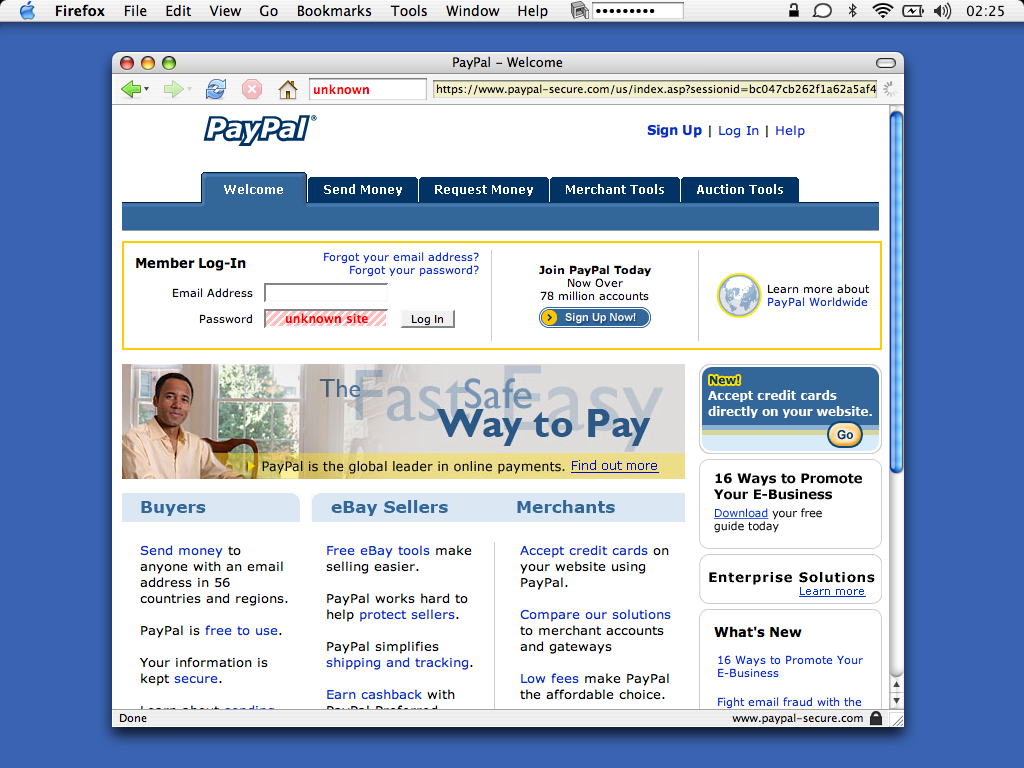
- Other password hashing schemes do prevent your password from getting captured, but don't protect you from impersonation. For example, if you use PwdHash (http://crypto.stanford.edu/PwdHash/), a phishing site can still accept your (hashed and useless) password, pretend to log in successfully, then ask you for your personal information. If you use passnames instead, the label in the location bar helps alert you to the fact that you're at the wrong site, and the password field will also be filled in with "unknown".
This is what a phishing attack would look like: